Security
As the following dataflow diagram shows, aha-secret has a very minimalistic design with just two forms. One for encryption and the other for decryption. A built-in ratelimit protects against misuse as a data storage and prevents enumeration or brute-force attacks. The developers try to minimize the dependencies to keep the chances for supply-chain-attacks as low as possible.
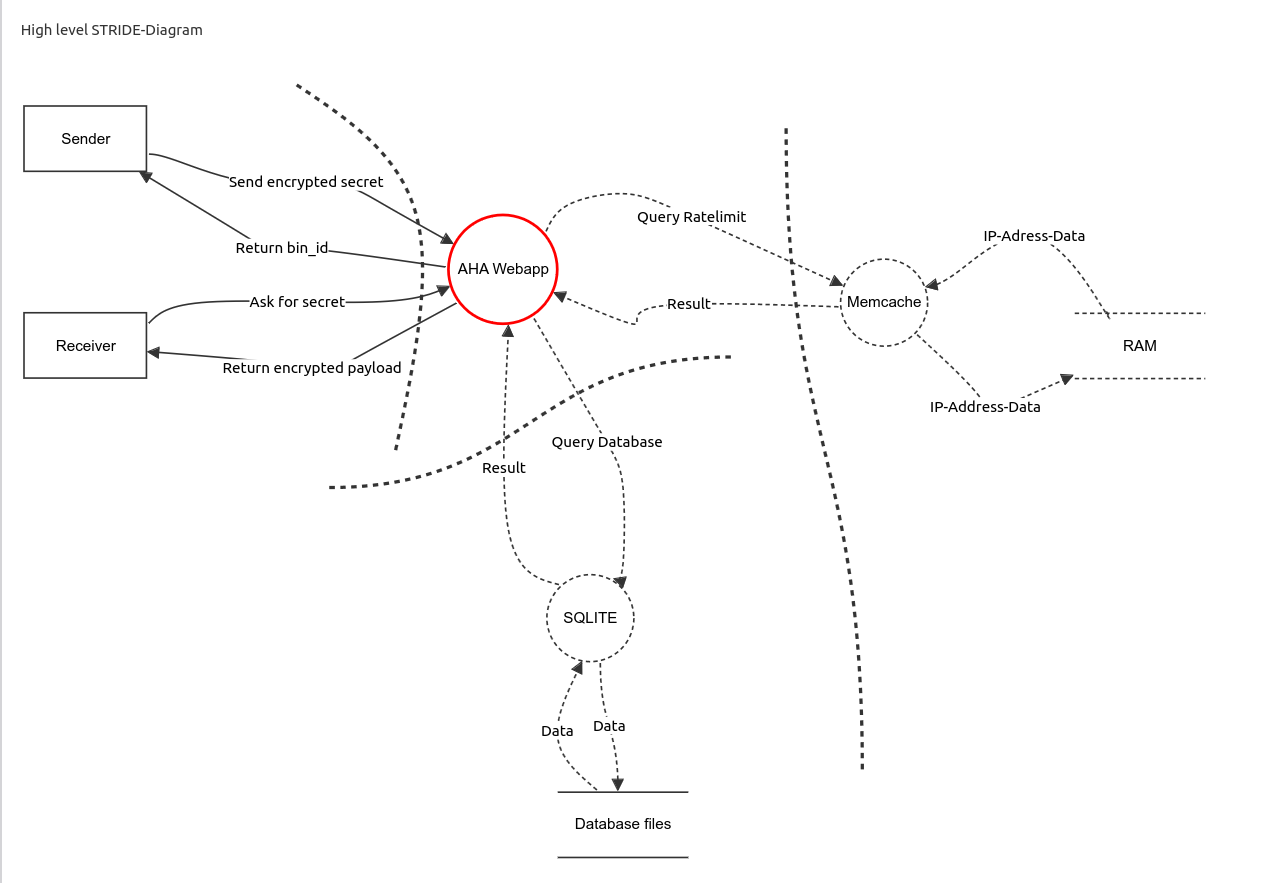
Please have a look at the full aha-secrets threat-model. It was made with OWASP Threat Dragon. Use this link to download the config of the threat model.